#Creates or updates the policy for a certificate in a key vault.
$Policy = New-AzKeyVaultCertificatePolicy -SecretContentType "application/x-pkcs12" -SubjectName "CN=adven.com" -IssuerName "Self" -ValidityInMonths 6 -ReuseKeyOnRenewal
#Adds a certificate to a key vault.
#Here TestCert01 is Certificate Name and hpvault01 is keyVault Name in
Add-AzKeyVaultCertificate -VaultName "hpvault01" -Name "TestCert01" -CertificatePolicy $Policy
# Gets the status of a certificate operation. Check the progress until its status is complete
$progress=(Get-AzKeyVaultCertificateOperation -VaultName "hpvault01" -name TestCert01).status
# Gets the secrets in a key vault.
$cert=Get-AzkeyvaultSecret -VaultName "hpvault01" -Name "TestCert01"
#Converts the specified string, which encodes binary data as base-64 digits, to an equivalent 8-bit unsigned integer array
$certBytes=[System.Convert]::FromBase64String($cert.SecretValueText)
# Write all Bytes to local computer C:\xfer Folder
[System.IO.File]::WriteAllBytes("C:\xfer\TestCert01",$certBytes)
$certCollection = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2Collection
$certCollection.Import($certBytes,$null,[System.Security.Cryptography.X509Certificates.X509KeyStorageFlags]::Exportable)
$certificateBytes = $certCollection.Export([System.Security.Cryptography.X509Certificates.X509ContentType]::Cert)
$name = $cert.Name
$cerName = $name.Replace('pfx','cer')
[System.IO.File]::WriteAllBytes("C:\xfer\$cerName", $certificateBytes)
Write-Host "Certificate created from Pfx and copied to local directory C:\xfer folder
Create an Application gateway using portal
Create a Managed identity using AZ CLI
--------------------------------------
$rgname = "newrakeshrg"
$location = "East US"
$kv = "hpvault01"
$appgwName = "prestigeappgateway"
$resourceGroup = New-AzResourceGroup -Name $rgname -Location $location
$identity = New-AzUserAssignedIdentity -Name "appgwKeyVaultIdentity" `
-Location $location -ResourceGroupName $rgname
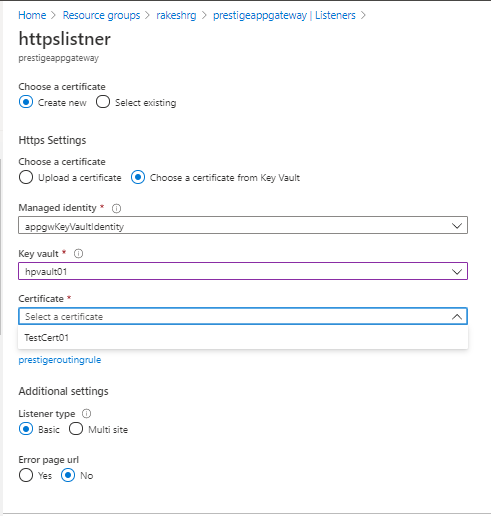
# Now associate the keyvault Certificate to Application gateway listener using portal

No comments:
Post a Comment