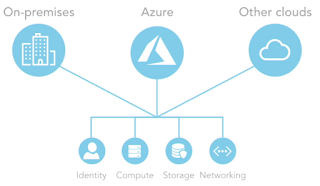
Delivered from the overall Microsoft Azure Cloud Service, the Microsoft Operations Management Suite or OMS enables you to gain visibility and control with comprehensive operations management and security across your on-premises data center, Azure, and other clouds.
Now recently, Microsoft decided to change the name from OMS to nomenclature that better describes the functions being used. The name will change to Microsoft Azure Management and Microsoft Azure Security,
Now recently, Microsoft decided to change the name from OMS to nomenclature that better describes the functions being used. The name will change to Microsoft Azure Management and Microsoft Azure Security,
However, at this time, the name hasn't changed, nor have the various infrastructure names as used in the Azure portal. They're still named OMS. Additionally, the documentation sites you use, such as docs.microsoft.com and the MSDN and TechNet websites, still list the overall area as OMS.
Azure divides the functionality of OMS into four key features.
==================================================
To that end, it is better to introduce the four key features that OMS brings to us and call them by these newer names.
- Azure Automation & Control
- Azure Insights & Analytics
- Azure Security & Compliance
- Azure Protection & Recovery
Azure Automation & Control
==========================
Now let's take a more detailed look at these new names that highlight the overall abilities and components that OMS is made out of.
First, we have Microsoft Azure automation and control.
This feature enables a consistent control and compliance through configuration, update management, and advanced change tracking.
It includes
- Automation configuration management
- Change tracking
- Update management
Coming to Azure insights and analytics
Azure insights and analytics
====================
Azure insights and analytics
====================
This feature gives you visibility across workloads, giving access to all the information needed on what's happening in the environment.
It includes
- Log analytics
- Service map
- Network performance monitor
Next we have Azure protection and recovery.
=================================
This feature allows you to ensure availability of important applications and data and keeps critical data protected with integrated cloud backup and site recovery.
It includes backup and Azure site recovery to Azure and to customer-owned sites.
And finally, Azure's security and compliance
================================
With this feature, you can drive security across your environment with sophisticated
threat intelligence capabilities,
malware detection, and
indicators of compromise.
This feature includes the
- Azure security center
- advanced security and audit functionality
- Malware threat analysis.
1.Azure Automation and Control
=======================
It enables continuous servicing and compliance with automation and configuration management.
It allows you to manage all automation and configuration assets from a centralized repository with detailed access control.
It allows you to manage all automation and configuration assets from a centralized repository with detailed access control.
This allows you to retain control of when and how to patch without having any unplanned down time and with the approval of the application owner.
It also allows you to resolve alerts and plan and conduct backup and disaster recovery using automated remediation scripts and recovery plans.
You can apply and monitor your configurations by using a highly available poll service and fix configuration drift without intervening manually. Finally, you can run automated processes from Azure or locally from an on-premises data center with hybrid runbook worker processing.
Azure IT Automation has the following functional abilities.
Establish responsive IT operations ->You can set up triggers to process on demand or automatically. This improves your response time by taking immediate action on operational issues.
Sustain consistent configuration-> You can avoid configuration drift by applying monitoring and automatically updating the desired state of your applications and infrastructure resources using a highly available poll service from Azure.
Maintain compliant IT resources-->This lets you combine change tracking with configuration management to identify and apply configurations and enable compliance.
Azure IT Automation has the following functional abilities.
Establish responsive IT operations ->You can set up triggers to process on demand or automatically. This improves your response time by taking immediate action on operational issues.
Sustain consistent configuration-> You can avoid configuration drift by applying monitoring and automatically updating the desired state of your applications and infrastructure resources using a highly available poll service from Azure.
Maintain compliant IT resources-->This lets you combine change tracking with configuration management to identify and apply configurations and enable compliance.
You can deliver orchestrated update management for Windows server and Linux from the Cloud.
Create automated delivery of services-> You can integrate process automation and configuration management for end to end automated delivery of services across your IT environment. Use across on-premises and Cloud.
You use familiar Power shell skills to automate complex and repetitive tasks. You can extend the Cloud automation capabilities to your on-premises data center without human intervention.
About Runbook
A Runbook is a set of tasks that perform some automated process in Azure Automation.
A runbook may be a simple process such as starting a virtual machine and creating a log entry or you may have a complex runbook that combines other smaller runbooks to perform a complex process across multiple resources or even multiple Clouds and on-premise environments.
As an example, you might have an existing manual process for truncating a SQL database transaction log if it's approaching maximum size.
That includes multiple steps that you'll have to configure.
1.Connecting to the server,
2.Connecting to the database
3.Getting the current size of the database
4.Check if the threshold has been exceeded
2.Connecting to the database
3.Getting the current size of the database
4.Check if the threshold has been exceeded
You will need to do this on every database server.
If the SQL server log is full, you will then have to perform a backup operation and truncate the log and finally, notify the user.
Instead of manually performing all of these steps, you can create a runbook that would perform all of them as a single task.
You would start the runbook, provide the required information such as the SQL server names, the database names, the recipient email, and then sit back while the process completes.
Runbooks are based on Windows Powershell or Windows Powershell workflow.
Runbooks can do anything that Powershell can do. If an application or service has an API, then a runbook can work with it.
If you have a Powershell module for the application, then you can move that module into Azure Automation and include those command notes in your runbook
Azure Automation Runbooks run on the Azure Cloud and can access any Cloud resource or external resource that can be accessed from the Cloud.
Sample powershell script
#Requires -Version 2
<#
Script to truncate SQL log file for one or more on current SQL server
If $DBName paramter is not provided, the script truncates log files of all user databases on this SQL server
Sam Boutros - 5 June 2014 - V1.0
28 July 2014 - V1.1 - Cosmetic re-write
20 January 2016 - v2.0 - rewrite for PS2
#>
#region Input
[CmdletBinding(ConfirmImpact='Low')]
Param(
[Parameter(Mandatory=$false)][String[]]$DBName # Example ('App1DB','App2DB'), if blank script truncates logs of all user DBs
)
#endregion
function Show-Database {
[CmdletBinding()]
Param([Parameter(Mandatory=$true)][String[]]$DBList)
$DBInfo = @()
foreach ($DBName in $DBList) {
$DBID = Invoke-Sqlcmd -Query "SELECT DB_ID(N'$DBName') AS [DBID]"
$LogFile = Invoke-Sqlcmd -Query "USE $DBName; SELECT * FROM sys.database_files" | where { $_.Physical_name -match 'ldf' }
$DBRecoveryModel = Invoke-Sqlcmd -Query "SELECT * FROM sys.databases WHERE name = '$DBName'"
$DBInfo += New-object -TypeName PSObject -Property @{
Name = $DBName
ID = $DBID.DBID
LogFileName = $LogFile.name
LogFilePath = $LogFile.Physical_Name
'LogSize(MB)' = '{0:N0}' -f ($(Get-Item -Path $LogFile.Physical_Name).Length/1MB)
RecoveryModel = $DBRecoveryModel.recovery_model_desc
}
}
$DBInfo | select Name, ID, RecoveryModel, LogFileName, 'LogSize(MB)', LogFilePath | sort name
}
# Load SQLPS PowerShell Module
$SavedPath = (Get-Location).Path
try {
'Loading PS module SQLPS..'
Import-Module SQLPS -DisableNameChecking -ErrorAction Stop
'done'
} catch {
throw 'Failed to load PS module SQLPS, stopping'
}
Set-Location -Path $SavedPath
$DBList = @()
if ($DBName.Count) {
$DBList = $DBName
} else {
Invoke-SQLCMD -Query "SELECT * FROM sysdatabases WHERE dbid > 4" | % { $DBList += $_.name }
}
"Truncating log files of the following databases:"
$DBInfo = Show-Database -DBList $DBList
$DBInfo | FT -a
$DBInfo | % {
"Truncating file $($_.LogFilePath)"
$Query = "USE [$($_.Name)]; "
if ($_.RecoveryModel -match 'SIMPLE') {
$Query += "DBCC SHRINKFILE(N'$($_.LogFileName)', 1); "
} else {
$Query += "ALTER DATABASE [$($_.Name)] SET RECOVERY SIMPLE WITH NO_WAIT; "
$Query += "DBCC SHRINKFILE(N'$($_.LogFileName)', 1); "
$Query += "ALTER DATABASE [$($_.Name)] SET RECOVERY $($_.RecoveryModel) WITH NO_WAIT "
}
Invoke-Sqlcmd -Query $Query | Out-Null
}
Show-Database -DBList $DBList | FT -a
# To schedule a Powershell script:
$ScriptPath = 'C:\Scripts\Truncate-SQL.ps1'
$TaskName = 'TruncateSQL'
$TaskRun = "powershell.exe -NoLogo -NonInteractive -WindowStyle Hidden -Command ""$ScriptPath"""
# Example: Weekly on Sundays at 2 AM
SCHTASKS.EXE /Create /S $Env:COMPUTERNAME /RU SYSTEM /SC WEEKLY /D SUN /TN $TaskName /TR $TaskRun /ST 02:00 /RL HIGHEST /F
break
# Example: Daily at 7 AM
SCHTASKS.EXE /Create /S $Env:COMPUTERNAME /RU SYSTEM /SC DAILY /TN $TaskName /TR $TaskRun /ST 07:00 /RL HIGHEST /F
break
# Run now:
SCHTASKS /Run /TN "\$TaskName"
break
<#
Use
SchTasks.exe /Create /?
To see switch details
#>
2.Insight and analytics
===============
===============
Insights and analytics brings your IT operational intelligence platform into the cloud, which makes it easier to gain valuable insight from multiple data sources, whether structured or unstructured.
Insight and analytics is built on the underlying logged analytic platform. Insight and analytics offers a superset of the capabilities offered under log analytics.
You can choose to use the raw log analytics capabilities and pay per-gigabyte in the service or switch your workspace to the insight and analytics tier and pay per-node, managed by the service.
Insight and analytics helps you analyze at the scale you need with high compute and storage capacity in Azure as well as monitor your network performance from the public cloud service to your on-premises endpoints.
Also, to further enhance insight and analytics, you can download several free solution packs from the Azure marketplace. Many other solutions, some quite advanced, are offered at cost.
The major functionality of Azure insight and analytics include the following
Transform machine data à This lets you bring all of your information together in a single view for actionable insight. You can collect, store, and analyse log data from virtually any Windows server and even Linux sources.
Get immediate insight-> You can interact with real-time data to get deep intelligence gathered from your on-premises and cloud data centers. You can map server and application dependencies to discover connections and interactions
Resolve incidents fasteràYou're able to spot problems fast using pre-built solutions and queries. You can address incidents quickly with flexible search, customize alerts in the portal, or from the mobile app.
3.Protection and Recovery
===================
===================
Azure protection and recovery-> Before we start the section, let's take a moment to once again talk about naming and nomenclature in Microsoft Azure. As told earlier, the Azure province of OMS is undergoing a name change to better reflect its functionality and its place in the Azure cloud service. Things can change rapidly in the Azure ecosystem. New ideas, processes, and functionality can be deployed to Azure as soon as they are available, which means things can change in a monthly, weekly, and even daily basis.
Because of this, name changes can be inevitable.
Azure might come up with an entire new function that also includes older functions or processes, and these will get a name change because of this new overall functionality. Protection for your virtual machines in Azure.
Because Azure is a leading hyperscale cloud provider with the most global data centers in the world, you can back up and restore or replicate and failover all your major apps and data from your choice of many regions.
Fabric level protection removes the time involved in installing an agent to enable backup. With integration into Azure virtual machine management, you can easily discover Azure backup and then quickly start protecting your workloads from day one.
Protection and recovery lets you back up and restore critical assets from an integrated cloud-based services. You can reduce the number of workloads on premises, in your overall infrastructure maintenance, we can reduce costs with powerful Azure recovery service tools, and pay-as-you-go storage.
You can use Azure site recovery to migrate to ensure and to protect workloads in the cloud. With Azure backup, you can deploy and maintain backups in the Azure portal, giving you one centralized location to manage your disaster recovery plans.
BCDR(Business continuity and disaster recovery(BCDR)
======================================
To better reflect the functionality here, Azure refers to this overall process as business continuity and disaster recovery, or BCDR.
BCDR is implemented through the Azure recovery services.
BCDR is implemented through the Azure recovery services.
There are two components included with Azure recovery services.
Site recovery service--> Site recovery helps enable business continuity by keeping your apps running on VMs and physical servers, available if the site goes down.
Site recovery service--> Site recovery helps enable business continuity by keeping your apps running on VMs and physical servers, available if the site goes down.
Site recovery replicates workloads running on VMs and physical servers, so that they remain available in a secondary location if the primary site isn't available.
It recovers workloads to the primary site when it's up and running again.
Azure Site recovery services
================
Site recovery offers the following benefits.
- Deploy a simple BCDR solution
- Replicate Azure VMs on-premises VMs off-site, and any workload
- Keep data resilient and secure
- Meet recovery time objectives, or RTO
- Recovery point objectives, or RPO
- keep apps consistent over failover
- Test without disruption
- Run flexible failovers
- Create recovery plans
- Integrate with existing BCDR technologies
- Integrate with the automation library, and manage network settings.
Backup service.
==============
In addition, the Azure backup service keeps your data safe and recoverable by backing it up to Azure.
Azure backup provides the following key benefits.
- Automated storage management,
- unlimited scaling
- multiple storage options
- unlimited data transfer
- data encryption
- application consistent backup
- long-term retention
Security and compliance
==============
==============
Azure Security and Complianceà Security and Compliance enable security across data center environments, including nodes in your on-premises datacenters and other cloud service providers. Azure Security and Compliance provides for the following benefits.
Benefits of Azure Security and Compliance
------------------------------------------------------------
Analyze and investigate incidents à You can use Azure Security and Compliance to analyze events across multiple data sources and identify security risks. This helps you to understand the scope and impact of threats and attacks to mitigate the damage of a security breach.
Detect threats before they happen-> You can identify attack patterns by visualizing outbound malicious IP traffic and threat types. Azure Security and Compliance helps you understand the security posture of your entire environment, regardless of the platform.
Streamlined security audits->This allows you to capture all of the log and event data required for security or compliance audits. You can reduce the time and resources that you need to do a security audit with a complete, searchable and exportable log to an event data set.
Automatic data collection àSave time and reduce effort to identify security event and threat data that you need to collect and analyze. Once you connect the agents, the service automatically selects and collects the necessary data.
Efficient data storage-> Regardless of how much the data increases in size, Azure Security and Compliance gives you the compute and storage capacity that you need. It also allows you to cost effectively monitor security events over longer periods for more accuracy and supply data for critical security audits.
A new component of Azure Security and Compliance service is the Azure Security Center.
The Azure Security Center has been created to provide unified security management and advanced threat protection for work loads running in Azure, on premises and in other clouds.
It delivers visibility and control over hybrid cloud workloads, activate defenses that reduce your exposure to threats and intelligent detection to help you keep pace with rapidly evolving cyber attacks.
Using the Azure Security Center gives you the feature benefits of unified visibility and control, adaptive threat protection and intelligent threat detection and response. Let's look at each on separate slides.
Unified visibility and control àThere are a number of features that you can use here such as understanding security state across hybrid workloads which allows you to manage all your hybrid cloud workloads on premises, Azure and other cloud platforms in one console.
Built-in dashboards provide instant insight into security issues that require attention.
- Visibility into cloud workloads à Automatically discover and onboard new resources created by your Azure subscriptions.
- A centralized policy managementà ensures compliance with company or regulatory security requirements by centrally managing security policies across all your hybrid cloud workloads.
- Security data from many sourcesàThis let's you collect, search and analyze security data from a variety of sources including connected partner solutions like network firewalls and other Microsoft services.
- Integration with existing security workflows à provide access, integration and analysis of security information using REST APIs to connect to existing tools and processes.
- Compliance reporting àUse security data and insights to demonstrate compliance and easily generate evidence for auditors.
Adaptive Threat Prevention
====================
The functions in this major process involve such capabilities as continuous security assessment, this lets you monitor the security of machines, networks and Azure services using hundreds of built-in purity assessments or create your own. It also identifies software configurations that are vulnerable to attacks.
- Actionable recommendations allow you to remediate security vulnerabilities before they can be exploited by attackers using prioritized actionable security recommendations and built-in automation playbooks.
- Adaptive application controls These controls can block malware and other unwanted applications by applying white listing recommendations adaptive to your specific Azure workloads and powered by machine learning.
- Network access security reduces the network attack surface just in time, controlled access to management ports on Azure virtual machines, drastically reducing exposure to brute force and other network attacks.
Intelligent threat detection and response.
Use advance analytics and the Microsoft Intelligent Security Graph and the Azure Security Center to get an edge over evolving cyber attacks. You can leverage built-in behavioral analytics and machine learning to identify attacks and zero day exploits. You can also monitor networks, machines and cloud services for incoming attacks and post-breach activity. This offers a streamlined investigation with interactive tools and contextual threat intelligence.
This overall process provides functionality with the following, industry's most extensive threat intelligence. This uses a Microsoft Intelligent Security Graph which uses trillions of signals from Microsoft services and systems around the globe to identify new and evolving threats.
Advance threat detection uses built-in, behavioral analytics and machine learning to identify attacks and zero day exploits. It also monitors networks, machines and cloud services for incoming attacks and post-breach activity.
Advance threat detection uses built-in, behavioral analytics and machine learning to identify attacks and zero day exploits. It also monitors networks, machines and cloud services for incoming attacks and post-breach activity.
Prioritize alerts and incidents focus on the most critical threats. First, with prioritize security alert and incidents that map alerts of different types into a single attack campaign. You can also create your own security alerts and prioritize them.
Streamlined investigation, this quickly assesses the scope and impact of an attack by providing a visual period of interactivity during the attack. You can use predefined or Ad-Hoc Queries for deeper exploration of security data.
Contextual threat intelligence. This visualizes the scope of attacks on an interactive world map. It uses built-in threat intelligence reports to gain valuable insight into the techniques and objectives of known malicious actors.
~ Co
Configure a Log Analytics service and workspace
In order to collect Log information, you must install the Microsoft Monitoring Agent or MMA on Windows or Linux computers. For Windows and Linux virtual machines already deployed in Azure, you install the MMA with the Log Analytics VM Extension. Using the extension simplifies the installation process and automatically configures the agent to send data to the Log Analytics workspace that you specify. The agent is also upgraded automatically ensuring that you have the latest features and fixes.
As shown above, we need to get the work space Id and
primary key.. hence go to advanced settings..
Primary Key :-
XXXXXwcJE0MNtKwjJPGrD2T2v8noWXXXXXXXXXXXXXXXE9TAlUru3+veFXXXXXXXUBny+w==
(Masked) do not use this..
Go to control panel of first Azure VM and you will find
Microsoft Monitoring Agent is installed..
Concept taken from LIL.
Log Analytics Service
OMS provides log analysis by using the log analytics feature. Log analytics helps you collect and analyze data that resources in your cloud and on-premises environments generate. It gives you real-time insight by using integrated search and custom dashboards to analyze millions of records across all of your workloads and servers, regardless of their physical location.
Enterprise administrators can add solutions to log analytics that delineate the data to be collected and the logic for its analysis.
At the center of log analytics is the OMS repository, which the Azure cloud hosts. You can configure data sources and add solutions to your subscription to collect data in the repository from connected sources. Data sources and solutions will each create different record types that have their own set of properties, but you can still analyze together by using queries to the repository. This allows you to use the same tools and methods to work with different kinds of data that different sources collect.
Hence Log Analytics Service
- Collect and analyze data used by on-premise and cloud resources
- Real-time insights through integrated search and custom dashboard
- Azure cloud hosts the OMS repository
Repository stores data from connected sources
Log analytics Connected sources are : the computers and other resources that generate data. These can include agents on Windows and Linux computers that connect directly, or they can be agents from a connected management group.
Log analytics can also collect data from Microsoft Azure storage.
Data sources are the different kinds of data collected from each connected source. These can include events and performance data from Windows and Linux agents, in addition to sources such as IS logs and custom text logs.
You can configure each data source that you want to collect, and the configuration is automatically delivered to each connected source.
Hence Log Analytics Service
- Connected sources are: Computers, VMs, and connected management group
- Data sources: event and performance data from the connected sources
Most of your interaction with log analytics will be through the OMS Portal, which runs in any browser. This portal provides you will access to configuration settings and to multiple tools that help you analyze and act on collected data. From the portal, you can use log searches to construct queries to analyze collected data.
You can also customize dashboards with graphical views of your most valuable searches and use solutions that provide additional functionality and analysis tools.
Log analytics provides a query syntax to retrieve and consolidate data quickly in the repository, and you can create and save log searches to analyze data directly in the OMS Portal, and you can run log searches automatically to create an alert if the results of the query indicate an important condition.
Hence in Log Analytics Service :
- OMS Portal provides management access to Log Analytics
- Log Analytics queries used to retrieve and format results
- Create and save complex queries in the OMS Portal
- Automate queries to generate alerts when particular results are returned
To analyze data outside of log analytics you can export the data from the OMS repository into tools such as Microsoft's Power BI or Excel.
You can also use the log search application program interface to build custom solutions that use log analytics or to integrate with other systems.
Solutions add functionality to log analytics. They primarily run in the cloud and provide analysis of data collected in the OMS repository.
They can also define new record types, which you can collect to analyze by using log searches, or by using the additional user interface provided by the solution in the OMS dashboard.
Solutions are available for a variety of functions, and you can easily search for available solutions and add them to your OMS workspace from the solutions gallery in the Marketplace. Many solutions will automatically deploy and start working immediately,
while others might require some additional configuration, and will need to be purchased.
Costs may vary. Log analytics deployment requirements are minimal because the Azure cloud hosts the central components. The components include the repository and the services that allow you to correlate and analyze collected data. You can access the OMS Portal from any browser, so there is no requirement for client software.
Configure a Log Analytics service and workspace
Idea here is you will search for log analytics but you will end up creating a OMS Workspace. So do not get confused..
In the list of resources, type Log Analytics. As you begin typing, the list filters based on your input. Select Log Analytics.
1. Click Create, and then select choices for the following items:
- Provide a name for the new OMS Workspace, such as RakeshOMSWorkspace.
· Select a Subscription to link to by selecting from the drop-down list if the default selected is not appropriate.
· For Resource Group, choose to use an existing resource group already setup or create a new one.
· Select an available Location. For more information, see which regions Log Analytics is available in.
· If you are creating a workspace in a new subscription created after April 2, 2018, it will automatically use the Per GBpricing plan and the option to select a pricing tier will not be available. If you are creating a workspace for an existing subscription created before April 2, or to subscription that was tied to an existing Enterprise Agreement (EA) enrollment, select your preferred pricing tier. For more information about the particular tiers, see Log Analytics Pricing Details.
1. After providing the required information on the OMS Workspace pane, click OK.
While the information is verified and the workspace is created, you can track its progress under Notifications from the menu.
Go to activity log you will find nothing
Hence important here is Install the MMA
You can collect data from your physical or virtual Windows computers and other resources in your environment by installing the MMA on them directly through the MMASetup-.exe program. Before installing the Microsoft Monitoring Agents for Windows, you need the Workspace ID and Primary Key for your Log Analytics workspace.
This information is required by the Setup Wizard to properly configure the agent and ensure it can successfully communicate with Log Analytics.
As previously stated, when you sign up for Log Analytics, Azure creates a workspace in OMS. You can think of the workspace as unique Microsoft OMS environment with its own data repository, data sources, and solutions. You can create multiple workspaces in your subscription to support multiple environments such as production and test environments. You will need to install and connect agents for all of the computers that you want to onboard in order for them to send data to the Log Analytics service and act on that data.
Each agent can report to multiple workspaces. On computers with internet connectivity, the agent uses the connection to the internet to send data to OMS. The agent uses TCPI port 443 to send encrypted information including event and performance data back to the OMS workspace. Since this port is usually open for secure web traffic, there is normally no issues about opening additional ports in the firewall.
When through connections to the internet are available to an on-premise system, the agent can connect to OMS to log data. In order to connect your Windows computers to OMS, you do these three simple steps. One, download the agent setup file from the OMS portal. Two, install the agent by running the setup program or using the command line. And three, configure the agent or add additional workspaces if necessary.
Azure Automation and Log Analytics use the OMS Gateway when connected or operational manager monitored computers do not have internet access. The OMS Gateway, which is an HTTP forward proxy that supports HTTP tunneling uses the HTTP CONNECT command, can collect data and send it to Azure Automation and Log Analytics on their behalf. The OMS Gateway supports the following: Windows computers with the MMA not directly connected to an OMS workspace, Linux computers with the OMS Agent for Linux not directly connected to an OMS workspace, System Center Operations Manager 2012 Service Pack One with Update Rollup seven, Operations Manager 2012 R2 with Update Rollup three, or Operations Manager 2016Management Group integrated with OMS.
You can use network load balancing to redirect and distribute the traffic across multiple gateway servers when you use the operations management groups. You should install the OMS agent on the computer running the network load balancing software.
Hence so how to install MMA
In order to install MMA go to logAnalytics Workspace in my case it is RakeshOMSWorkspace à In RakeshOMSWorkspace go to Workpace Data Source à
Select the VM from data source and click on the Connect à
Click on the connect, if the VM is in stop state, you will
get error..
Hence start the VM.. and then click on connect on
OMSworkspace
You will find OMS Connection either connecting or this
workspace..
WorkSpace Id :- 1df88418-21d3-4798-b049-de0c115ae042
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
If you have onpremise Server or desktop, you have to
download windows agent (64) from Advanced settings and execute it..
In my Windows10 local laptop machine, I am executing a file..
MMASetup-AMD64.exe
This is a end of Installing MMA
Next is Analyzing the Log Analytics data. -- Coming soon.





















1 comment:
Thank you for sharing this post.
devops Online Training
Post a Comment